
Introduction
In today’s digital landscape, where data breaches and cyber attacks are on the rise, organizations face constant threats to their security. To protect valuable assets, it is essential to employ proactive security measures such as vulnerability assessment and penetration testing. These two crucial components of a robust cybersecurity strategy can help businesses identify and remediate vulnerabilities before malicious actors exploit them. In this blog post, we will delve into the world of vulnerability assessment and penetration testing, exploring their significance, processes, and benefits.
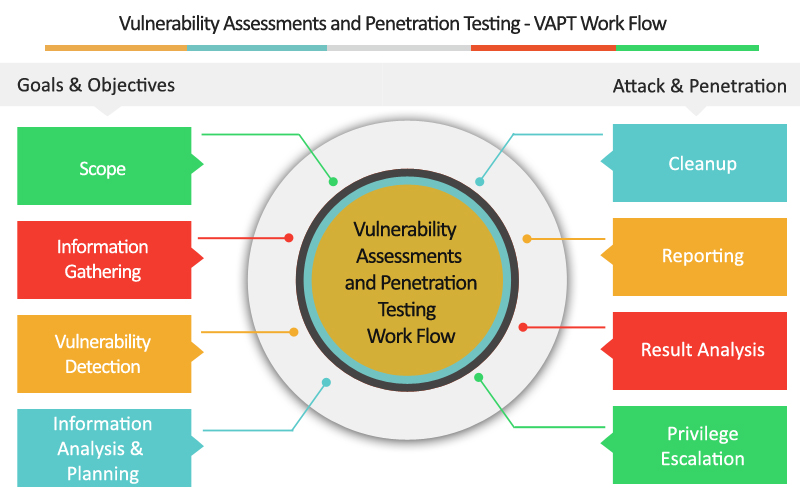
Understanding Vulnerability Assessment:
Vulnerability assessment is a systematic approach to identify security weaknesses and vulnerabilities within an organization’s systems, applications, and networks. This process involves the use of automated tools to scan and analyze various components for potential vulnerabilities. It examines factors such as misconfigurations, outdated software, weak passwords, and unpatched systems that could be exploited by attackers.
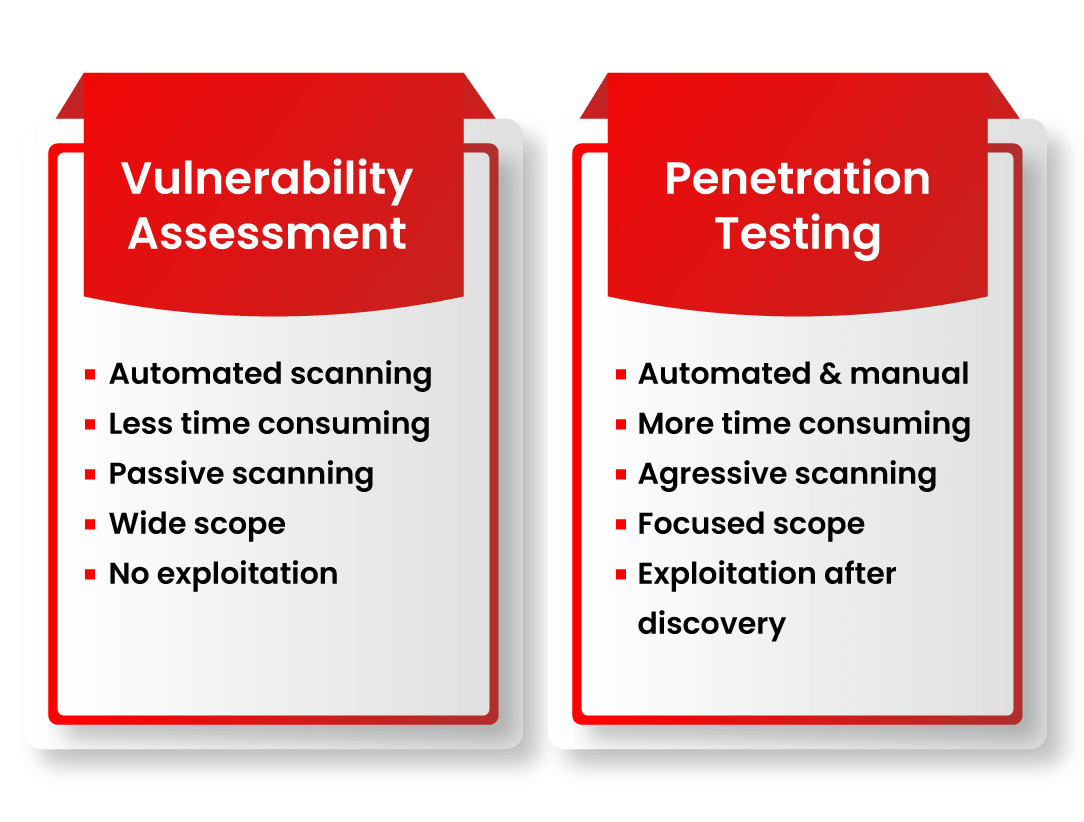
The primary objective of vulnerability assessment is to create a comprehensive inventory of vulnerabilities and provide organizations with actionable insights to mitigate those risks effectively. By conducting regular vulnerability assessments, businesses can stay one step ahead of potential threats, minimize the attack surface, and fortify their security posture.
The Role of Penetration Testing:
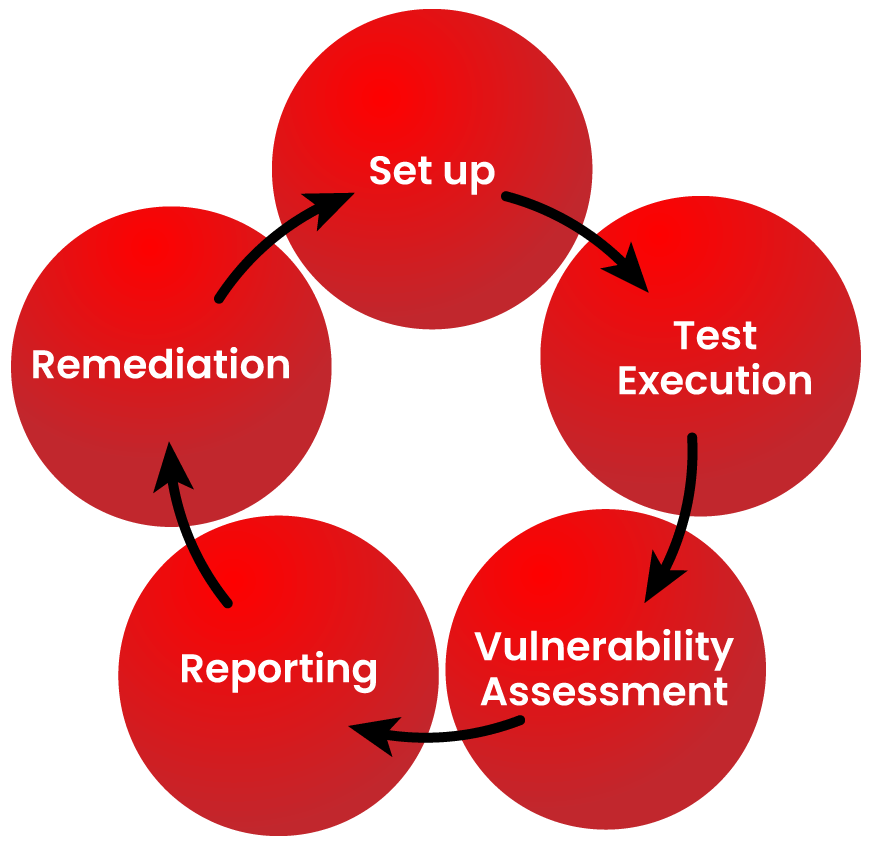
While vulnerability assessments help identify vulnerabilities, penetration testing takes the process a step further by actively simulating real-world attacks. Also known as ethical hacking, penetration testing involves authorized security professionals attempting to exploit identified vulnerabilities to determine the effectiveness of an organization’s security measures.
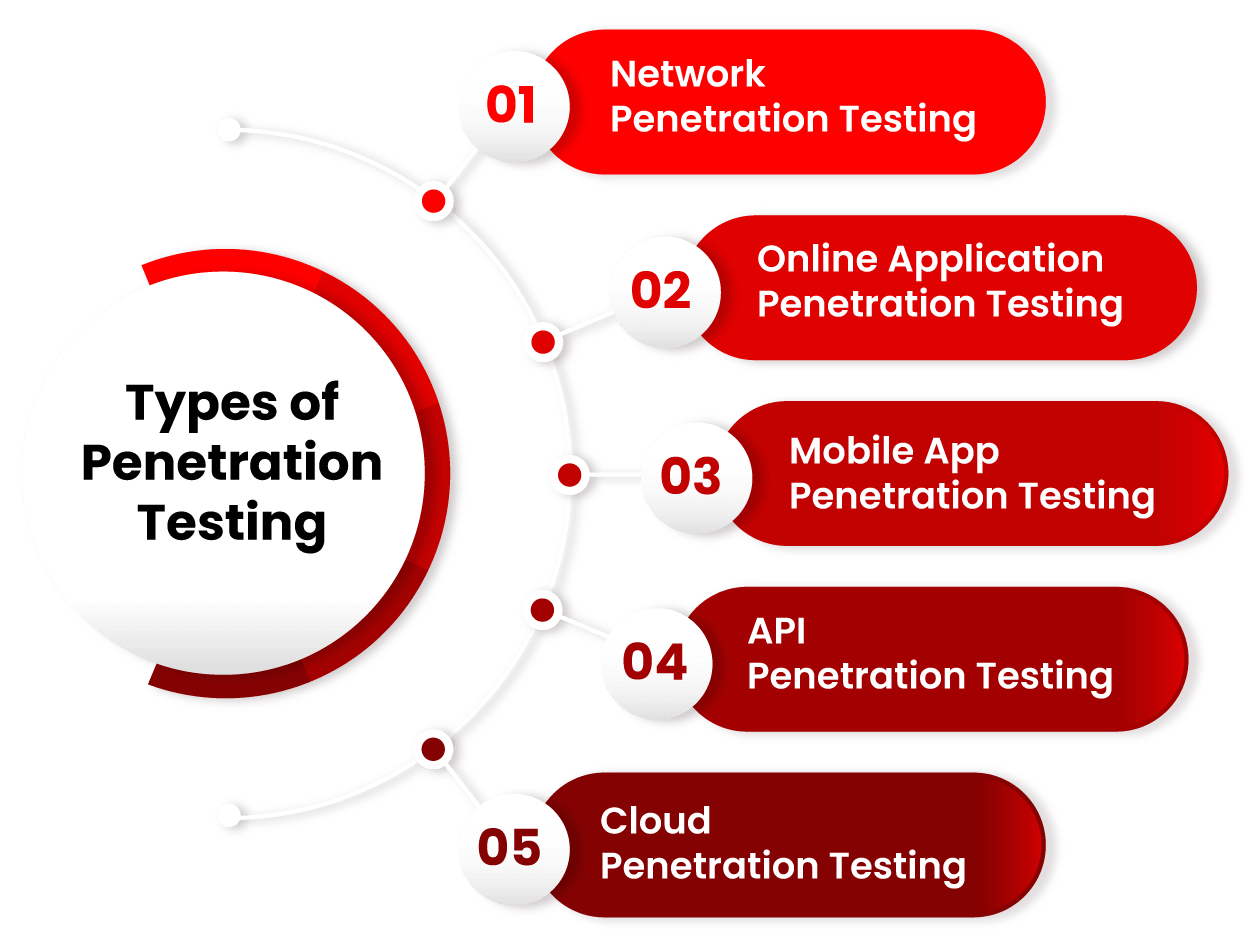
By conducting penetration tests, businesses can assess the resilience of their systems, applications, and networks against sophisticated attacks. Penetration testing provides valuable insights into the effectiveness of existing security controls, helps uncover unknown vulnerabilities, and validates the overall security strategy. It also enables organizations to prioritize remediation efforts based on the severity and potential impact of identified vulnerabilities.
Benefits of Vulnerability Assessment and Penetration Testing:
- Proactive Risk Management: By conducting regular vulnerability assessments and penetration tests, organizations can proactively identify and address security weaknesses, reducing the risk of successful attacks.
- Enhanced Security Posture: By understanding vulnerabilities and potential attack vectors, businesses can take appropriate measures to strengthen their security infrastructure, patch vulnerabilities, and apply necessary updates.
- Compliance and Regulatory Requirements: Many industries have specific compliance standards that organizations must adhere to. Vulnerability assessments and penetration testing help meet these requirements and demonstrate due diligence in safeguarding sensitive information.
- Protection of Brand Reputation: A successful cyber attack can tarnish a company’s reputation and erode customer trust. Regular testing helps prevent breaches and demonstrates a commitment to security, enhancing brand reputation.
- Cost Savings: Identifying and addressing vulnerabilities at an early stage is more cost-effective than dealing with the aftermath of a successful cyber attack. Vulnerability assessments and penetration testing help mitigate potential financial losses associated with data breaches.
Conclusion:
In an increasingly interconnected world, where cyber threats continue to evolve, vulnerability assessment and penetration testing play vital roles in protecting businesses from potential harm. By systematically assessing vulnerabilities, identifying weaknesses, and testing security defenses, organizations can enhance their security posture and minimize the risk of successful attacks. Embracing these proactive measures helps create a resilient cybersecurity framework, safeguarding critical assets and ensuring business continuity in the face of an ever-evolving threat landscape.
