
Introduction
In today’s interconnected world, where technology is deeply ingrained in every aspect of business operations, organizations face an ever-expanding attack surface. An attack surface refers to the sum of all potential entry points that can be exploited by malicious actors to compromise an organization’s digital assets. Attack Surface Management (ASM) is a proactive approach that helps businesses identify, assess, and mitigate vulnerabilities within their attack surface. In this blog post, we will explore the significance of Attack Surface Management, its key components, and the benefits it offers in safeguarding your organization.
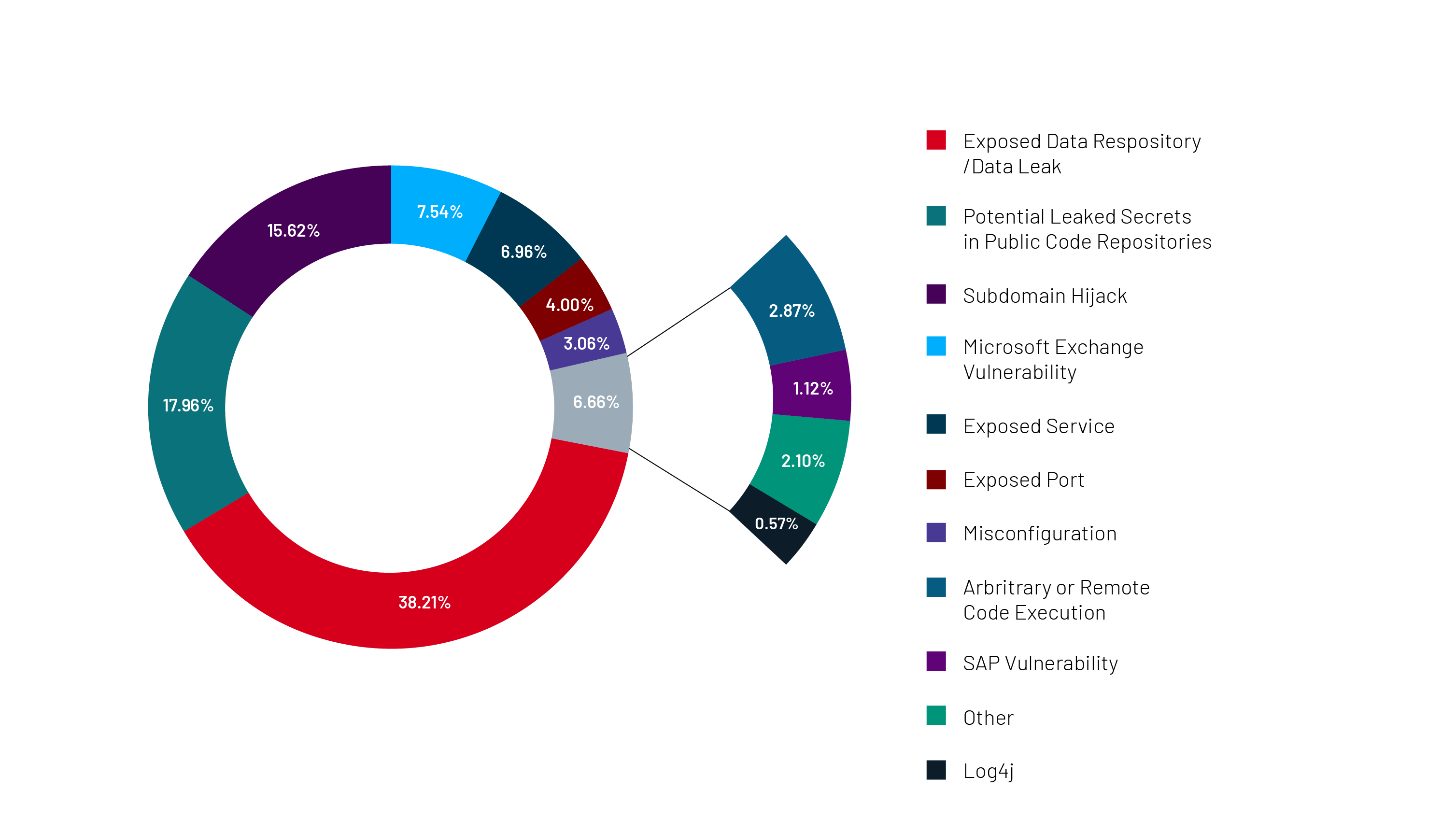
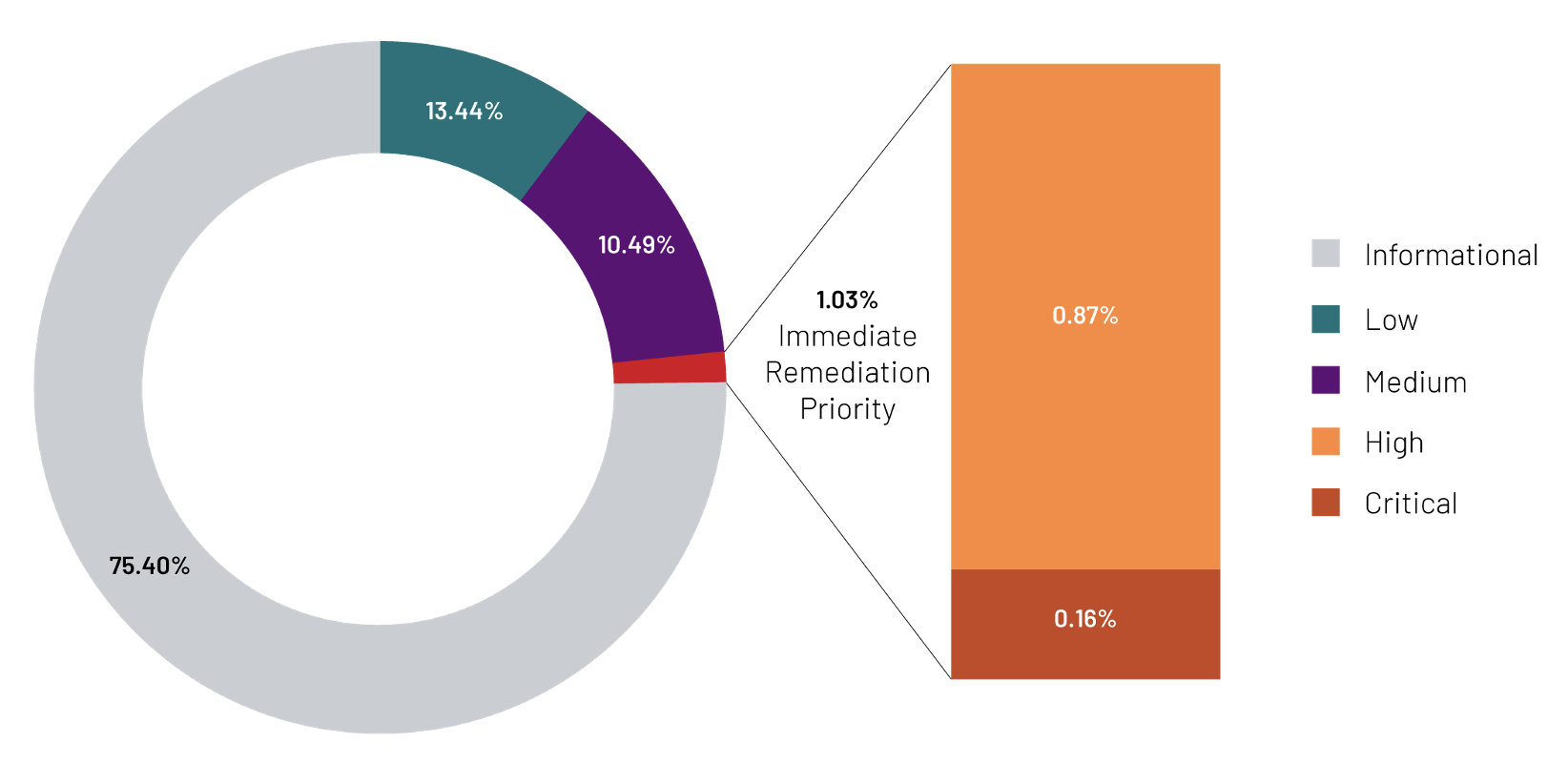
Understanding Attack Surface Management:
Attack Surface Management is a systematic process that involves identifying and managing all the possible entry points, vulnerabilities, and potential risks within an organization’s IT infrastructure, applications, networks, and systems. It aims to reduce the attack surface by minimizing the number of potential targets available to attackers.
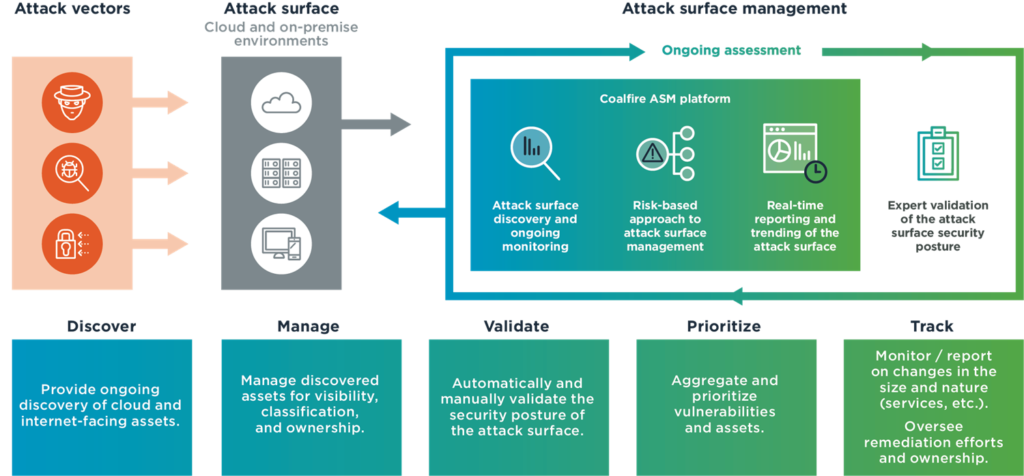
Key Components of Attack Surface Management:
- Attack Surface Discovery: This phase involves comprehensive mapping and discovery of an organization’s attack surface, including external-facing assets such as websites, web applications, APIs, and cloud resources, as well as internal assets like servers, databases, and IoT devices. Automated tools and manual techniques are utilized to gather information about these assets.
- Attack Surface Analysis: Once the attack surface is identified, it is analyzed to evaluate potential vulnerabilities and weaknesses. This includes vulnerability scanning, penetration testing, threat modeling, and risk assessment. By understanding the vulnerabilities present within the attack surface, organizations can prioritize remediation efforts.
- Attack Surface Reduction: In this phase, organizations take proactive measures to reduce the attack surface by implementing security controls, patching vulnerabilities, removing unnecessary services, and minimizing the exposure of critical assets. This includes implementing strong access controls, regular patching, and monitoring for new vulnerabilities.
Benefits of Attack Surface Management:
- Improved Security Posture: Attack Surface Management allows organizations to gain a comprehensive understanding of their potential vulnerabilities and take proactive measures to address them. By reducing the attack surface, organizations can significantly improve their security posture and minimize the risk of successful cyber attacks.
- Efficient Resource Allocation: By identifying and prioritizing vulnerabilities within the attack surface, organizations can allocate their resources effectively. This enables them to focus on the most critical areas and ensure that remediation efforts are targeted and efficient.
- Regulatory Compliance: Many industries have specific compliance requirements that organizations must meet. Attack Surface Management helps organizations stay compliant by identifying vulnerabilities and implementing necessary controls to mitigate risks.
- Enhanced Incident Response: By proactively managing the attack surface, organizations are better prepared to respond to security incidents. They can quickly identify and address vulnerabilities, reducing the impact of potential breaches and minimizing downtime.
- Protection of Brand Reputation: A successful cyber attack can have severe consequences for an organization’s brand reputation. Attack Surface Management helps prevent data breaches, showcasing a commitment to security and earning the trust of customers and stakeholders.
Conclusion:
In an evolving threat landscape, Attack Surface Management is an essential practice for organizations to safeguard their digital assets. By identifying and mitigating vulnerabilities within the attack surface, organizations can significantly reduce the risk of successful attacks. Implementing a proactive Attack Surface Management strategy enables businesses to enhance their security posture, meet regulatory requirements, and protect their brand reputation. Embrace Attack Surface Management as a crucial element of your cybersecurity strategy and fortify your organization against emerging threats.
